SomeWhereOverTheRainBow
Part of the Furniture
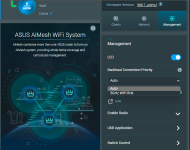
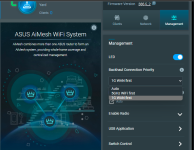
Pick a process, almost any process and dump it. They all have the same "Tainted:" information being displayed.
Code:killall -s SEGV dnsmasq killall -s SEGV vsftpd killall -s SEGV miniupnpd killall -s SEGV vnstatdCode:Jun 29 14:08:14 kernel: CPU: 1 PID: 18692 Comm: dnsmasq Tainted: P O 4.1.52 #2 Jun 29 14:09:07 kernel: CPU: 3 PID: 3251 Comm: vsftpd Tainted: P O 4.1.52 #2 Jun 29 14:10:30 kernel: CPU: 0 PID: 3259 Comm: miniupnpd Tainted: P O 4.1.52 #2 Jun 29 14:12:54 kernel: CPU: 2 PID: 3213 Comm: vnstatd Tainted: P O 4.1.52 #2
Code:
for i in $(seq 18); do echo $(($i-1)) $(($(cat /proc/sys/kernel/tainted)>>($i-1)&1));donewhat does this return for you.