What's the IP of Rocky-Corsair?
I'd also like to see the output of flexqos debug since I'm wondering if the special chars your rule names are breaking something. You shouldn't be seeing Untracked if it's matching the Non-Gaming UDP rule.
the rule works perfect if i set it up for Gaming instead of net control.
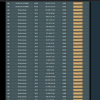
This is the debug when its classified to Gaming
Debug:
Log date: 2020-09-19 00:31:59+0800
Router Model: RT-AC68U
Firmware Ver: 384.19_0
tc WAN iface: eth0
Undf Prio: 2
Undf FlowID: 1:12
Classes Present: 8
Down Band: 51200
Up Band : 20480
***********
Net Control: 1:10
Work-From-Home: 1:16
Gaming: 1:11
Others: 1:12
Web Surfing: 1:14
Streaming: 1:15
File Downloads: 1:13
Game Downloads: 1:17
***********
Downrates: 2560, 15360, 2560, 2560, 2560, 2560, 2560, 2560
Downceils: 51200, 51200, 51200, 51200, 51200, 51200, 51200, 40960
Downbursts: 3200b, 12796b, 6400b, 3200b, 3198b, 3198b, 3200b, 3200b
DownCbursts: 64000b, 64000b, 64000b, 64000b, 64000b, 64000b, 64000b, 63994b
DownQuantums: default, default, default, default, default, default, default, default
***********
Uprates: 1024, 6144, 1024, 1024, 1024, 1024, 1024, 1024
Upceils: 14336, 14336, 14336, 14336, 14336, 14336, 14336, 14336
Upbursts: 3200b, 4798b, 3198b, 3200b, 3198b, 3198b, 3198b, 3200b
UpCbursts: 25Kb, 25Kb, 25Kb, 25Kb, 25Kb, 25Kb, 25Kb, 25Kb
UpQuantums: default, default, default, default, default, default, default, default
***********
iptables settings: <192.168.1.128/30>>udp>>!80,443>000000>1<>>tcp>>!80,443>000000>7<>>both>>80,443>>7<192.168.1.0/25>>udp>>!80,443>000000>7
-o br0 -d 192.168.1.128/30 -p udp -m multiport ! --sports 80,443 -m mark --mark 0x80000000/0xc03fffff -j MARK --set-mark 0x8008ffff/0x3fffff
-o eth0 -s 192.168.1.128/30 -p udp -m multiport ! --dports 80,443 -m mark --mark 0x40000000/0xc03fffff -j MARK --set-mark 0x4008ffff/0x3fffff
-o br0 -p tcp -m multiport ! --sports 80,443 -m mark --mark 0x80000000/0xc03fffff -j MARK --set-mark 0x803fffff/0x3fffff
-o eth0 -p tcp -m multiport ! --dports 80,443 -m mark --mark 0x40000000/0xc03fffff -j MARK --set-mark 0x403fffff/0x3fffff
-o br0 -p tcp -m multiport --sports 80,443 -j MARK --set-mark 0x803fffff/0x3fffff
-o br0 -p udp -m multiport --sports 80,443 -j MARK --set-mark 0x803fffff/0x3fffff
-o eth0 -p tcp -m multiport --dports 80,443 -j MARK --set-mark 0x403fffff/0x3fffff
-o eth0 -p udp -m multiport --dports 80,443 -j MARK --set-mark 0x403fffff/0x3fffff
-o br0 -d 192.168.1.0/25 -p udp -m multiport ! --sports 80,443 -m mark --mark 0x80000000/0xc03fffff -j MARK --set-mark 0x803fffff/0x3fffff
-o eth0 -s 192.168.1.0/25 -p udp -m multiport ! --dports 80,443 -m mark --mark 0x40000000/0xc03fffff -j MARK --set-mark 0x403fffff/0x3fffff
***********
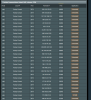
appdb rules: <000000>6<00****>7<09****>7<12****>7<0D****>7<14****>7<04****>7<06****>7<05****>7<13****>7<03****>7<18****>7
filter add dev br0 protocol all prio 2 u32 match mark 0x80000000 0xc000ffff flowid 1:12
filter add dev eth0 protocol all prio 2 u32 match mark 0x40000000 0xc000ffff flowid 1:12
filter change dev br0 prio 3 protocol all handle 822::800 u32 flowid 1:17
filter change dev eth0 prio 3 protocol all handle 822::800 u32 flowid 1:17
filter change dev br0 prio 12 protocol all handle 803::800 u32 flowid 1:17
filter change dev eth0 prio 12 protocol all handle 803::800 u32 flowid 1:17
filter change dev br0 prio 21 protocol all handle 801::800 u32 flowid 1:17
filter change dev eth0 prio 21 protocol all handle 801::800 u32 flowid 1:17
filter change dev br0 prio 16 protocol all handle 81e::800 u32 flowid 1:17
filter change dev eth0 prio 16 protocol all handle 81e::800 u32 flowid 1:17
filter change dev br0 prio 23 protocol all handle 804::800 u32 flowid 1:17
filter change dev eth0 prio 23 protocol all handle 804::800 u32 flowid 1:17
filter change dev br0 prio 7 protocol all handle 821::800 u32 flowid 1:17
filter change dev eth0 prio 7 protocol all handle 821::800 u32 flowid 1:17
filter change dev br0 prio 9 protocol all handle 824::800 u32 flowid 1:17
filter change dev eth0 prio 9 protocol all handle 824::800 u32 flowid 1:17
filter change dev br0 prio 8 protocol all handle 823::800 u32 flowid 1:17
filter change dev eth0 prio 8 protocol all handle 823::800 u32 flowid 1:17
filter change dev br0 prio 22 protocol all handle 802::800 u32 flowid 1:17
filter change dev eth0 prio 22 protocol all handle 802::800 u32 flowid 1:17
filter change dev br0 prio 6 protocol all handle 80c::800 u32 flowid 1:17
filter change dev eth0 prio 6 protocol all handle 80c::800 u32 flowid 1:17
filter change dev br0 prio 27 protocol all handle 81f::800 u32 flowid 1:17
filter change dev eth0 prio 27 protocol all handle 81f::800 u32 flowid 1:17
[/CODE][/SPOILER]
admin@RT-AC68U-E990:/tmp/home/root#
admin@RT-AC68U-E990:/tmp/home/root#