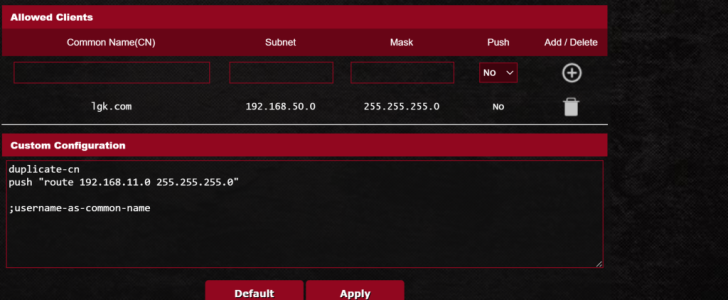
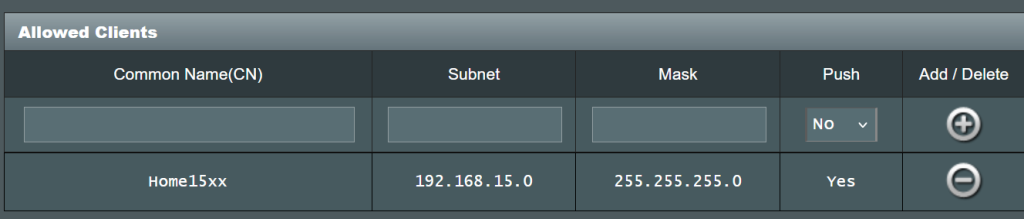
iBest
Occasional Visitor
Just PM me. If it makes it easier, post the dumps to PasteBIn and provide links.
ifconfig
ip route
ip route show table ovpnc1
ip route show table ovpnc2
ip route show table ovpnc3
ip route show table ovpnc4
ip route show table ovpnc5
brctl show
ip rule
cat /tmp/etc/openvpn/client1/config.ovpn
cat /tmp/etc/openvpn/client2/config.ovpn
cat /tmp/etc/openvpn/client3/config.ovpn
cat /tmp/etc/openvpn/client4/config.ovpn
cat /tmp/etc/openvpn/client5/config.ovpn
cat /tmp/etc/openvpn/server1/config.ovpn
cat /tmp/etc/openvpn/server2/config.ovpn
cat /jffs/openvpn/vpndirector_rulelist
iptables -vnL
iptables -t nat -vnL
Man I did the logs .... but it's impossible to share all this info...
It's not about wan ip or mac addresses; it's also all ciphers from vpn, all profiles ... everything ...
I have logs from both fw now. If you can be more specific (you or any staff member), i can take data from logs, mask it, and share here.... but just can't upload this on internet.
I am sorry