If they are not errors then why were they flooding my log? "Errors" or just standard messages, the result was the same, a good number of them being reported in the log that stopped when I removed the dnsmasq-sdn.postconf script file and went back to using dnsmasq-1.conf.add and dnsmasq-2.conf.add files.Those are not errors.
Beta Asuswrt-Merlin 3006.102.4 Beta is now available
- Thread starter RMerlin
- Start date
dave14305
Part of the Furniture
Something earlier in the log was restarting dnsmasq. That part of the log might give clues.If they are not errors then why were they flooding my log? "Errors" or just standard messages, the result was the same, a good number of them being reported in the log that stopped when I removed the dnsmasq-sdn.postconf script file and went back to using dnsmasq-1.conf.add and dnsmasq-2.conf.add files.
Let me ask, why are you manually editing files? Can't you assign IPs under GNP in the Advanced Settings? I have this
In addition to the limit of 32 manual assignments in the GNP GUI for VLANs mentioned by @bennor (which seems to be further constrained by nvram, so I never managed to even get to 32, got stuck at 21), because of this.
I resorted to using the same dnsmasq-x.config.add file edits as bennor, approaching it like this.
Last edited:
Agree. A few being sufficient if you limit it to "a few"; in my case 21, which is quite a few, but less than 32.It'll be helpful for those that want to do this for a few guest devices
Last edited:
I confirm that observation in my setup. Maybe by design if limited by nvram.While using the dnsmasq-snd.conf.add file to add manual IP reservations for the Guest Network Pro, those entries are not reflected in the Manually Assign IP around DHCP list option
dave14305
Part of the Furniture
There’s no connection between Merlin custom config files and the GNP GUi developed by Asus. The GUI reads nvram variables to populate. conf.add files don’t impact nvram.I confirm that observation in my setup. Maybe by design if limited by nvram.
Thank you for that, explains really nicely what goes on under the hood, so explains the observations more general users such as myself see at the surfaceThere’s no connection between Merlin custom config files and the GNP GUi developed by Asus. The GUI reads nvram variables to populate. conf.add files don’t impact nvram.
The Guest Network Pro option to Manually Assign IP Address around the DHCP List appears to store the manual client information in at least the two following locations (there may be others). In the following examples I used a second Customized Network (53), MAC address redacted.
In the NVRAM:
In the /etc/dnsmasq-2.conf file:
In the NVRAM:
dhcpres2_rl=<AA:BB:CC:DD:EE:FF>192.168.53.100>>12MyPhoneIn the /etc/dnsmasq-2.conf file:
dhcp-host=AA:BB:CC:DD:EE:FF,set:AA:BB:CC:DD:EE:FF,12MyPhone,192.168.53.100dave14305
Part of the Furniture
The GUI stores the settings in the nvram variable for its SDN index number (2 in your example). The firmware reads it from nvram and creates the temporary dnsmasq-2.conf file so that the dedicated dnsmasq instance knows what to do for that network. The /etc/dnsmasq-2.conf file is not persistent and is rewritten after every dnsmasq restart or router reboot.The Guest Network Pro option to Manually Assign IP Address around the DHCP List appears to store the manual client information in at least the two following locations (there may be others).
I'm trying not to be too annoying (with varying degrees of success and failure), but want to help ensure as many users as possible understand how complicated third-party customization is becoming with 3006 and its newfound flexibility. The more power users, the better.
The /etc/dnsmasq-2.conf file is not persistent and is rewritten after every dnsmasq restart or router reboot.
Not sure where in NVRAM (used to be dhcp_staticlist), but just to drill down into the possibilities here:In the NVRAM:
dhcpres2_rl=<AA:BB:CC:DD:EE:FF>192.168.53.100>>12MyPhone
Despite it not being persistent in dnsnasq-x.conf, if someone wanted to use NVRAM (whatever the file in NVRAM is called) to save/add/amend manual assignments, that would then automagically appear in the GNP GUI for a specific VLAN, this is doable?
I actually looked (not very hard) for that file a while back but couldn’t find one when I searched for a test MAC Address or Hostnames that I had put into the GUI.
Last edited:
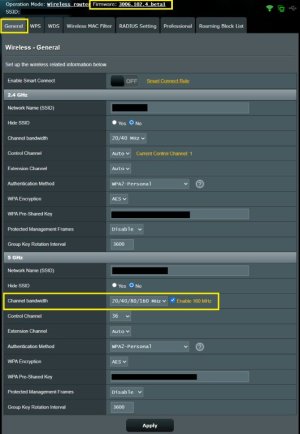
I upgraded the GT-AX11000 Pro from the stock 3.0.0.6.102_34750 to the beta version and noticed the 160 MHz options were all missing in the wireless settings. Specifically, the checkbox "enable 160MHz" was not there and the drop down for channel bandwidth did not have 20/40/80/160 option. It showed a 20/40/80 option. Sorry I didn't capture a screenshot. I went back to factory, rebooted, and went through the upgrade again, same result. I did not do a factory reset. Interesting the wireless logs did show that 160 MHz was functioning when I selected the 20/40/80 drop down option.
bbunge
Part of the Furniture
You may have to clear the web browser cache. Also a very good idea to factory reset after upgrading to Merlin firmware and manually configuring.I upgraded the GT-AX11000 Pro from the stock 3.0.0.6.102_34750 to the beta version and noticed the 160 MHz options were all missing in the wireless settings. Specifically, the checkbox "enable 160MHz" was not there and the drop down for channel bandwidth did not have 20/40/80/160 option. It showed a 20/40/80 option. Sorry I didn't capture a screenshot. I went back to factory, rebooted, and went through the upgrade again, same result. I did not do a factory reset. Interesting the wireless logs did show that 160 MHz was functioning when I selected the 20/40/80 drop down option.
alekc_oc
Occasional Visitor
This setting now is in the Professional section of Wireless settings 5GHz.I upgraded the GT-AX11000 Pro from the stock 3.0.0.6.102_34750 to the beta version and noticed the 160 MHz options were all missing in the wireless settings. Specifically, the checkbox "enable 160MHz" was not there and the drop down for channel bandwidth did not have 20/40/80/160 option. It showed a 20/40/80 option. Sorry I didn't capture a screenshot. I went back to factory, rebooted, and went through the upgrade again, same result. I did not do a factory reset. Interesting the wireless logs did show that 160 MHz was functioning when I selected the 20/40/80 drop down option.
MDM
Very Senior Member
No it's not, only Wireless Mode and 802.11ax / WiFi 6 mode are.This setting now is in the Professional section of Wireless settings 5GHz.
Channel Bandwidth and Enable 160 MHz still on the Wireless > General tab for me on a RT-AX86U Pro running the beta1.This setting now is in the Professional section of Wireless settings 5GHz.
Attachments
alan6854321
Senior Member
Same for me on a RT-AX88U_ProChannel Bandwidth and Enable 160 MHz still on the Wireless > General tab for me on a RT-AX86U Pro running the beta1.
The VPN page seems to be messed up for me. Have a RT-AX86U Pro. On the VPN Director Page I can select a client and/or rule hit Apply and it shows that nothing is selected even though it may be or I can deselect something and refresh page and it will show as still selected even though it isn't . The VPN may be working but it doesn't show it is. Went back to last Release firmware and all is fine. I tried clearing Browser cache and all that. I did not try deleting all VPN and re-adding them or setting router backs to defaults and starting over, as that would have been more work that I want to do right now.
Thanks...
Thanks...
GWTechTalk
Occasional Visitor
Found a couple issues that I don't know if they are contributed to this fork or basic ASUS firmware.
Neither one of these are huge issues. I used a command to eliminate the iPhone 13 from even getting band steering requests at all by putting it on a deny / exempt list. Possible idea for a GUI feature for older devices putting them on a band steering exempt list when there are like 10 more more rejects for the device?
For the PHY 30 issue it comes and goes and can be suppressed with some simple SSH commands. Ultimately, the PHY 30 should be tagged to the debug log not the warnings logs.
Other than that this beta is actually going well. No major problems, no connections issues, and no crashes. I'm curiously looking into the ddosmem errors on start up and seeing what exactly they mean and if they can or need to be suppressed or moved to "debug" logging tags. Over all I'm more of a power user than a true developer but I have a good amount of experience working with OpenWRT and designing custom micro routers out of SBCs. I really am a stickler for clean logging as logging is, IMO, the best way to troubleshoot or monitor device environments.
Hey, side bar question the newish feature of MAC randomization, is there anyway in the negotiating process for the network to force that feature to OFF? Apple has OFF, Fixed, RANDOM and Android has something similar. I have had to get clever with my home internet control for my kids so that when a previously unknown MAC address is on the router it's automatically puts the device into the most restrictive access group and I have to manual pull it out after checking the device has this feature off. Chrome, while an internet browser, has the external Safe search API feature than can be enforced from the DNS filter, such as Ad Guard Home, or PiHole.
Correcting one statement in here. Seems that ALL Apple iOS devices seem to reject or not respond to the bsd.
- BE96U doesn't appear to have a PHY 30 device. Currently Im seeing scans periodically which produce an error.
- kernel: enet_ioctl_compat_ethctl:L1984 No PHY type PHY_TYPE_UNKNOWN at address 30 has been found.
- iPhone 13 does not like and even rejects at times, band steering.
- bsd: bsd: wl0.1 Sending act Frame to REDACTED with transition target wl2.1 ssid REDACTED
bsd: bsd: BSS Transit Response: ifname=wl0.1, event=156, token=1, status=1, mac=00:00:00:00:00:00
bsd: bsd: BSS Transit Response: STA reject
- bsd: bsd: wl0.1 Sending act Frame to REDACTED with transition target wl2.1 ssid REDACTED
Neither one of these are huge issues. I used a command to eliminate the iPhone 13 from even getting band steering requests at all by putting it on a deny / exempt list. Possible idea for a GUI feature for older devices putting them on a band steering exempt list when there are like 10 more more rejects for the device?
For the PHY 30 issue it comes and goes and can be suppressed with some simple SSH commands. Ultimately, the PHY 30 should be tagged to the debug log not the warnings logs.
Other than that this beta is actually going well. No major problems, no connections issues, and no crashes. I'm curiously looking into the ddosmem errors on start up and seeing what exactly they mean and if they can or need to be suppressed or moved to "debug" logging tags. Over all I'm more of a power user than a true developer but I have a good amount of experience working with OpenWRT and designing custom micro routers out of SBCs. I really am a stickler for clean logging as logging is, IMO, the best way to troubleshoot or monitor device environments.
Hey, side bar question the newish feature of MAC randomization, is there anyway in the negotiating process for the network to force that feature to OFF? Apple has OFF, Fixed, RANDOM and Android has something similar. I have had to get clever with my home internet control for my kids so that when a previously unknown MAC address is on the router it's automatically puts the device into the most restrictive access group and I have to manual pull it out after checking the device has this feature off. Chrome, while an internet browser, has the external Safe search API feature than can be enforced from the DNS filter, such as Ad Guard Home, or PiHole.
Correcting one statement in here. Seems that ALL Apple iOS devices seem to reject or not respond to the bsd.
Last edited:
5stringdeath
Regular Contributor
I have the same router and mine is displaying / working fine. I'm only using Wireguard fwiwThe VPN page seems to be messed up for me. Have a RT-AX86U Pro. On the VPN Director Page I can select a client and/or rule hit Apply and it shows that nothing is selected even though it may be or I can deselect something and refresh page and it will show as still selected even though it isn't . The VPN may be working but it doesn't show it is. Went back to last Release firmware and all is fine. I tried clearing Browser cache and all that. I did not try deleting all VPN and re-adding them or setting router backs to defaults and starting over, as that would have been more work that I want to do right now.
Thanks...
Did you have to re-do the VPNs or reset router to defaults or anything like that? I might try again later or wait for Beta 2. I never did try any of the Alphas.I have the same router and mine is displaying / working fine. I'm only using Wireguard fwiw
Thanks
Similar threads
- Replies
- 112
- Views
- 10K
- Replies
- 161
- Views
- 15K
- Replies
- 313
- Views
- 32K
- Locked
- Replies
- 53
- Views
- 7K
- Replies
- 120
- Views
- 21K
Similar threads
Similar threads
-
Release Asuswrt-Merlin 3006.102.3 is now available for WIfi 7 devices
- Started by RMerlin
- Replies: 120
-
Beta Asuswrt-Merlin 3006.102.3 beta is now available for Wifi 7 devices
- Started by RMerlin
- Replies: 53
-
Asuswrt Merlin 3006.102.3 Alpha2 for GT-BE98 Pro, RT-BE86U, RT-BE88U, and RT-BE96U
- Started by visortgw
- Replies: 16
-
-
Release Asuswrt-Merlin 3006.102.2 is now available for Wifi 7 devices
- Started by RMerlin
- Replies: 101
-
Beta Asuswrt-Merlin 3006.102.2 Beta is now available for Wifi 7 devices
- Started by RMerlin
- Replies: 70
-
Release Asuswrt-Merlin 3006.102.1 is now available for Wifi 7 devices
- Started by RMerlin
- Replies: 106
-
Beta Asuswrt-Merlin 3006.102.1 Beta is now available for WIfi 7 devices
- Started by RMerlin
- Replies: 97
-
-
Does Asuswrt-Merlin support Kill-Switch and Auto-Reconnect etc ?
- Started by alphaswe
- Replies: 0
Latest threads
-
Release ASUS RT-AX52 Firmware version 3.0.0.4.388_33911 (2025/04/25)
- Started by fruitcornbread
- Replies: 0
-
Release ASUS RT-AX1800S V2 Firmware version 3.0.0.4.388_33911 (2025/04/24)
- Started by fruitcornbread
- Replies: 0
-
-
Anyone successfully using Parental Controls - Time Scheduling on an ASUS router right now?
- Started by pcb
- Replies: 0
-
Guest network pro firmware on dsl ax82u
- Started by octopulse
- Replies: 4
Support SNBForums w/ Amazon
If you'd like to support SNBForums, just use this link and buy anything on Amazon. Thanks!
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!