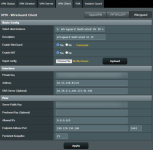
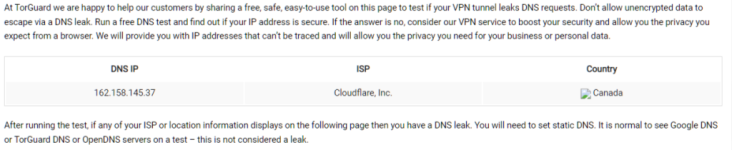
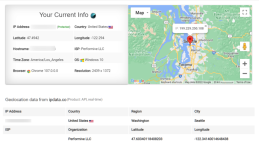
I ran into an issue with DNS again. Torguard seems to have no idea why this is happening to me. That doesn't mean they are not part of the problem though, at this point. I'll present this to you people for a look. This morning I checked Wireguard's status. It was running so I did some tests on the Torgaurd site. I did a "what's my IP" and a DNS leak test as well as WebRTC test. See results below. The DNS test shows Cloudflare. Cloudflare is my DNS-over-TLS choice. As you can see I have two Torguard DNS servers configured into the client (see config below). Torguard and I are unable to figure out why the DNS fails or is diverted to the Routers DNS, with a failover of theirs in the config of the Wireguard client. Any ideas people?
@RMerlin ?
UPDATE: Torguard says its the router over riding the Wireguard DNS selection, it could be the client itself or the DNS Director possibly.
UPDATE 2: I added a DNS Director rule last night before I checked this, this morning. The DNS Director rule was to force one of the Wireguard attached devices to use the DNS-over-TLS DNS (Cloudflare) configured on the router. Maybe the Wireguard client needs to be restarted as part of the applying of this new rule. Restarting the client straightened out the DNS problem.