SomeWhereOverTheRainBow
Part of the Furniture
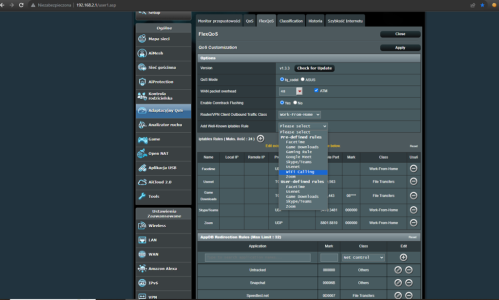
I am not an oldtimer nor do I understand reading this stuff, but here is what ChatGPT says.Any old timers know what this means, especially at 5108?
Code:0000000000005000 <fc_hook_cb>: 5000: a9af7bfd stp x29, x30, [sp, #-272]! 5004: 910003fd mov x29, sp 5008: f9000bf3 str x19, [sp, #16] 500c: 90000013 adrp x19, 0 <__stack_chk_guard> 5010: 91000273 add x19, x19, #0x0 5014: b90027ff str wzr, [sp, #36] 5018: f9400262 ldr x2, [x19] 501c: f90087e2 str x2, [sp, #264] 5020: d2800002 mov x2, #0x0 // #0 5024: b4000a00 cbz x0, 5164 <fc_hook_cb+0x164> 5028: 90000003 adrp x3, 100 <forward_find_ct_by_tuples+0x100> 502c: 91000063 add x3, x3, #0x0 5030: aa0003e2 mov x2, x0 5034: aa0103e4 mov x4, x1 5038: 91006063 add x3, x3, #0x18 503c: 90000001 adrp x1, 100 <forward_find_ct_by_tuples+0x100> 5040: 91000021 add x1, x1, #0x0 5044: 52800020 mov w0, #0x1 // #1 5048: 94000000 bl 0 <__ll_sc_atomic_add> 504c: a902ffff stp xzr, xzr, [sp, #40] 5050: 92400440 and x0, x2, #0x3 5054: f1000c1f cmp x0, #0x3 5058: a903ffff stp xzr, xzr, [sp, #56] 505c: a904ffff stp xzr, xzr, [sp, #72] 5060: a905ffff stp xzr, xzr, [sp, #88] 5064: a906ffff stp xzr, xzr, [sp, #104] 5068: a907ffff stp xzr, xzr, [sp, #120] 506c: a908ffff stp xzr, xzr, [sp, #136] 5070: a909ffff stp xzr, xzr, [sp, #152] 5074: a90affff stp xzr, xzr, [sp, #168] 5078: a90bffff stp xzr, xzr, [sp, #184] 507c: a90cffff stp xzr, xzr, [sp, #200] 5080: a90dffff stp xzr, xzr, [sp, #216] 5084: a90effff stp xzr, xzr, [sp, #232] 5088: a90fffff stp xzr, xzr, [sp, #248] 508c: 540004e0 b.eq 5128 <fc_hook_cb+0x128> // b.none 5090: f9403041 ldr x1, [x2, #96] 5094: b25963e0 mov x0, #0xffffff8000000000 // #-549755813888 5098: eb00003f cmp x1, x0 509c: 54000368 b.hi 5108 <fc_hook_cb+0x108> // b.pmore 50a0: 52800000 mov w0, #0x0 // #0 50a4: d2800005 mov x5, #0x0 // #0 50a8: 52800002 mov w2, #0x0 // #0 50ac: b941f887 ldr w7, [x4, #504] 50b0: 32000006 orr w6, w0, #0x1 50b4: 121f7801 and w1, w0, #0xfffffffe 50b8: 910093e4 add x4, sp, #0x24 50bc: 528000a3 mov w3, #0x5 // #5 50c0: 9100a3e0 add x0, sp, #0x28 50c4: f24000ff tst x7, #0x1 50c8: f9003fe5 str x5, [sp, #120] 50cc: 1a860021 csel w1, w1, w6, eq // eq = none 50d0: 290a0be1 stp w1, w2, [sp, #80] 50d4: f9004be4 str x4, [sp, #144] 50d8: b900bbe3 str w3, [sp, #184] 50dc: 94000000 bl 0 <udb_shell_do_fastpath_action> 50e0: 7100001f cmp w0, #0x0 50e4: 52800061 mov w1, #0x3 // #3 50e8: 1a9f0020 csel w0, w1, wzr, eq // eq = none 50ec: f94087e2 ldr x2, [sp, #264] 50f0: f9400261 ldr x1, [x19] 50f4: ca010041 eor x1, x2, x1 50f8: b5000341 cbnz x1, 5160 <fc_hook_cb+0x160> 50fc: f9400bf3 ldr x19, [sp, #16] 5100: a8d17bfd ldp x29, x30, [sp], #272 5104: d65f03c0 ret 5108: b9406c20 ldr w0, [x1, #108] 510c: 91018045 add x5, x2, #0x60 5110: b9006040 str w0, [x2, #96] 5114: b9405842 ldr w2, [x2, #88] 5118: 52800000 mov w0, #0x0 // #0 511c: b9410821 ldr w1, [x1, #264] 5120: b90027e1 str w1, [sp, #36] 5124: 17ffffe2 b 50ac <fc_hook_cb+0xac> 5128: 927ef442 and x2, x2, #0xfffffffffffffffc 512c: b25963e1 mov x1, #0xffffff8000000000 // #-549755813888 5130: f9401040 ldr x0, [x2, #32] 5134: eb01001f cmp x0, x1 5138: 54fffb49 b.ls 50a0 <fc_hook_cb+0xa0> // b.plast 513c: b9406c01 ldr w1, [x0, #108] 5140: 91008045 add x5, x2, #0x20 5144: f9001041 str x1, [x2, #32] 5148: b9401842 ldr w2, [x2, #24] 514c: b9410800 ldr w0, [x0, #264] 5150: b90027e0 str w0, [sp, #36] 5154: d3405c42 ubfx x2, x2, #0, #24 5158: b94053e0 ldr w0, [sp, #80] 515c: 17ffffd4 b 50ac <fc_hook_cb+0xac> 5160: 94000000 bl 0 <__stack_chk_fail> 5164: 90000000 adrp x0, 0 <forward_find_ct_by_tuples> 5168: 91000000 add x0, x0, #0x0 516c: 94000000 bl 0 <printk> 5170: 52800000 mov w0, #0x0 // #0 5174: 17ffffde b 50ec <fc_hook_cb+0xec> 5178: d503201f nop 517c: d503201f nop
The instruction b9406c20 is an ARM64 instruction that loads a 32-bit (4-byte) word from memory into the W0 register. The specific addressing mode used here is [x1, #108], which means it is attempting to load a 32-bit word from the memory location pointed to by register X1 plus an offset of 108 bytes.
The instruction itself appears to be correct in terms of its syntax. However, what's "wrong" with it depends on the context of your code and the intended purpose of this operation. Here are some considerations:
To determine what's specifically "wrong" with this instruction, you'll need to consider the larger context of your code, such as the values in registers (x1 in this case) and the purpose of the loaded data. Additionally, you should verify that the memory access is within bounds and properly aligned.
- Memory Access: Make sure that the memory location [x1, #108] is valid and accessible. If x1 doesn't point to a valid memory location, or if the offset of 108 bytes goes beyond the boundaries of the memory region pointed to by x1, it could lead to memory access violations.
- Data Alignment: In ARM64, memory access operations often require proper data alignment. Ensure that the memory location pointed to by x1 is properly aligned for a 32-bit load operation. Unaligned memory accesses can lead to performance penalties or even crashes on some architectures.
- Register Usage: Be aware of the intended use of the data loaded into w0 and make sure it aligns with the logic of your program. If the data is supposed to be used elsewhere in the code, verify that it's used correctly.
- Error Handling: Depending on the context, you may want to check for errors or exceptions related to this memory access. For example, you might want to add code to handle cases where the memory access fails.
But you cannot go by the reliability of chatgpt. I wonder if @RMerlin understands any of this stuff, or @dave14305 for that matter..