lilstone87
Very Senior Member
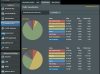
@FreshJR Here's a image of what the "Traffic classification" page looked like while the download was running. Oddly no large amounts of data shows on the download side. However the upload side it oddly shows 300KB's of data being passed over "Gaming", Which I would think should of been under "Game Transferring" as it relates to the game update being downloaded. Something is for sure off.
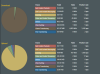
Also here's what the "Bandwidth monitor" page showed while the download was running. I don't know what to say.. I don't have any custom rules running either. I just have the one game rule that's already there, attached to my PS4's internal IP/32.
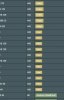
EDIT: Well I removed my PS4's IP from the Gaming rule that is set by default. I started the download back up, and it actually showed the download under "Game Transferring". Look at Traffic Classification 2 image. Still I don't like how the upload data being passed by the game download, is showing under "Gaming" though.
Also here's what the "Bandwidth monitor" page showed while the download was running. I don't know what to say.. I don't have any custom rules running either. I just have the one game rule that's already there, attached to my PS4's internal IP/32.
EDIT: Well I removed my PS4's IP from the Gaming rule that is set by default. I started the download back up, and it actually showed the download under "Game Transferring". Look at Traffic Classification 2 image. Still I don't like how the upload data being passed by the game download, is showing under "Gaming" though.
Attachments
Last edited: